Cyber security has become an increasingly prominent focus of the industry. Regulators also are taking a strong interest in understanding and assessing regulated firms’ resilience to cyber-attacks. This article provides a brief overview of existing high-level cyber risk management tools, which hedge fund managers (and others) can use to develop their tailored approach to cyber security, a framework to identify a firm’s key digital assets (“crown jewels”), a list of practical “quick win cyber security action items”, and an overview of “cyber security projects” to enhance a firm’s resilience, including the development of an “Incident Response Plan”. Where possible, this article refers to widely accepted resources, as well as additional guidance particularly suitable for small and medium-sized firms. The last section focuses on “what regulators want to see” in terms of cyber risk preparedness, including an overview of regulatory requirements, guidance and approaches to cyber security for a number of key jurisdictions.
Introduction
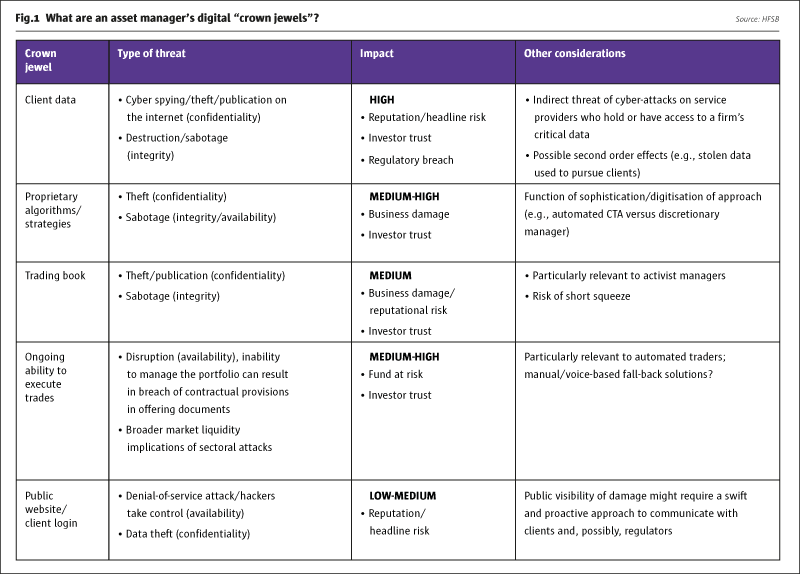
Cyber crime is defined as “a harmful activity, executed by one group or individual through computers, IT systems and/or the internet and targeting the computers, IT infrastructure and internet presence of another entity”. The motives behind cyber-attacks can be manifold, ranging from fraud, espionage (nation states, terrorists), “hacktivism” (motivated by political motives), insider sabotage or theft, or disruption (for fun). Regulators are particularly concerned about the wider systemic consequences of cyber crime (e.g., massive reputational damage across entire sectors, and effects on market availability and integrity). Cyber security threats will vary in nature and scale as a function of an organisation’s vulnerabilities and “crown jewels” (confidential information, personal data of customers, critical systems, proprietary algorithms, trading book) and vulnerabilities.
These “crown jewels” also will differ significantly by type of firm. For example, the availability of an online banking platform may be integral to the value proposition of a retail bank (and integral to the clients’ trust), while the (possibly static) website of an institutional asset manager may play a much less important role in delivering the firm’s services. In fact, different business units within an organisation may view different types of data/infrastructure as critical. Therefore, a clear understanding of the firm’s ”crown jewels” and the impact of a cyber-attack on them are the first steps in determining the types of protections an organisation needs. Fig.1 lists some typical “crown jewels”, though the list is not exhaustive.
CLICK IMAGE TO ENLARGE
Various surveys indicate that over 60% of threats are caused by “people issues” (such as use of weak log-in credentials, phishing, disgruntled employees, etc.), rather than technological failures. This highlights the fact that cyber security is not just an IT issue but requires a much broader approach and ownership within organisations – “tone from the top” and a culture of ownership of cyber risk throughout an organisation are critical.
High-level cyber risk tools and guidance
Many resources exist to help firms structure their approach to addressing cyber risks, including cross-sectoral frameworks, such as the NIST Framework and the ISO/IEC 27000-series security standards. In addition, there are certification standards, such as COBIT and the Cyber Essentials frameworks in the UK. Some of the cyber risk management tools and guidance are very general in nature but can help a firm to formulate and structure its overarching cyber security strategy and principles, while others are more “hands-on” and provide lists of explicit cyber security “to dos”.
The challenge usually lies in translating these tools into relevant action, tailored to the specific risk profile of an organisation. In particular for medium-sized and smaller organisations, it is important to develop a targeted and efficient approach to address cyber security risks. The next section below has extracted from the above-mentioned tools and guidance some of the most important aspects relevant to hedge fund managers and put them into a set of (i) technical cyber security “action items” and (ii) an overview of cyber security projects (including “questions to ask”).
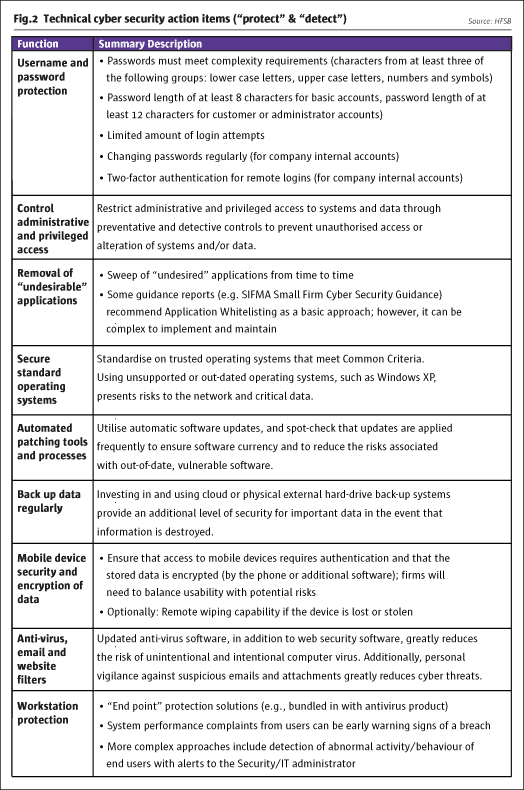
Practical steps/“quick wins”
While cyber-attacks are becoming more sophisticated, most breaches can be prevented relatively easily. There are a number of low-cost measures that are fairly simple to implement and can reduce significantly the impact of attacks.
There are also a number of broader projects hedge fund managers can undertake to develop a more tailored approach to addressing cyber security threats. Of particular relevance in this context is the development of an Incident Response Plan, which may tie in with a firm’s (1) broader disaster recovery measures (see Hedge Fund Standard 17d) and (2) IT security framework (see Hedge Fund Standard 17f). Fig.3 provides an overview of different projects hedge fund managers can undertake, including “questions to ask”.

CLICK IMAGE TO ENLARGE
It is important to note that in areas where there is significant reliance on third-party service providers in the supply chain, such as custody, prime brokerage and independent administration of assets, it may be unrealistic to assume that a hedge fund manager can conduct in-depth due diligence on the cyber security measures implemented by such suppliers. However, firms can assess/monitor where service providers are given limited access to their own technology systems that inadvertently may enable unauthorised access to data/systems and actively manage the risk accordingly. In addition, firms should consider whether they require a minimum level of disclosure from any service provider with respect to that provider’s own cyber security risk management procedures and their effectiveness.
What do regulators want to see?
With the increasing regulatory focus on cyber security threats, firms want to better understand the level of security that is deemed sufficient to meet regulatory obligations. It is broadly acknowledged that a detailed and prescriptive approach to “regulating” cyber security will not work, given both the pace of technological innovation (in terms of the types of threats and protections), and the fact that there cannot be a “one size fits all” approach. Regulators have taken different approaches to address cyber security concerns. Some focus explicitly on the management arrangements to address cyber-threats (including risk assessments, information security policies, training, business continuity planning) and have issued specific guidance materials. Others have a more principle-based approach, whereby cyber security is covered by the broader conduct obligations and existing operational risk management arrangements.
The US Securities and Exchange Commission (SEC), for example, has started to focus on cyber security-related issues at regulated investment adviser and broker-dealer firms. In April 2014, the SEC’s Office of Compliance Inspections and Examinations (OCIE) announced its Cyber Security Initiative in a National Exam Program (NEP) Risk Alert. The recently published Examination Sweep Summary provides an overview on the areas of focus, including:
- Cyber security governance and oversight;
- Policies, procedures and training;
- Protection of networks and information;
- Client remote access and risks associated with fund transfer requests;
- Risks associated with third parties/vendors;
- Protocols for reporting cyber breaches.
The SEC’s OCIE also published its Investment Management Cyber Security Guidance in April 2015, which focuses on the measures firms may wish to consider, including:
- Periodic assessment of sensitivity/location of information, technology systems, internal and external threats, security controls, impact of breaches, effectiveness of governance arrangements;
- Development of a strategy to prevent/detect cyber security threats;
- Written policies and procedures, training.
In addition, the SEC’s OCIE published a Risk Alert (9/2015), highlighting some of the areas of focus for the second round of examinations. The Risk Alert indicates that there will be more testing of the firms’ procedures and controls and explicitly mentions protection of customer information as an area of focus. It also contains a sample list of materials the SEC’s OCIE may review during examinations.
The approach of the UK Financial Conduct Authority (FCA) is anchored in the FCA’s Principles for Business, notably Principle Three (Management and Control).More details are included in the provisions of The Senior Management Arrangements and Controls (SYSC) Sourcebook (SYSC 3 Systems and Controls, SYSC 6.3 Financial Crime [mostly focused on money laundering] and SYSC 21.1 Risk Control). Areas covered include the regular review of systems and controls and risk-centric governance arrangements. In addition, the FCA’s Principle 11 (Relations with regulators) may imply regulatory notification obligations (also see SUP 15: Notifications to the FCA or PRA). The FCA also provides a “One-minute guide” focusing specifically on (customer) data security (applicable to all regulated firms), including a Data Security Factsheet, which highlights aspects such as:
- Governance, compliance monitoring, training;
- Systems and control, including physical safety of data, disposal of data;
- Vetting of staff (e.g., credit checks, criminal record checks);
- Due diligence of third-party service providers, staff awareness.
Many other regulators have started to develop guidance and other resources to address cyber security concerns, and firms, which operate across multiple jurisdictions, need to be aware of these developments.
In light of the fast-evolving nature of the threats and the limitations of prescriptive rules and regulations to mitigate them, financial regulators and other government agencies also have started to conduct cyber-attack simulations and surveys to better assess the threats, as well as the mitigants that have been put in place to address those threats. While many of these efforts are cross-sectoral, some have a specific focus on attacks on financial market entities (e.g., Operation Waking Shark in the UK: focus on wholesale/investment banking and key financial market infrastructure). These efforts are equally relevant to hedge fund managers and investors, since they help enhance the understanding of how individual firms can be indirectly impacted by disruptions of key financial infrastructure and service providers (e.g., investment banks, custodians, exchanges, central depositories, etc.). They also give an idea of the types of safeguards firms might wish to put in place to deal with such scenarios.
How to get started?
The following recommendations may help firms develop a cyber security strategy based on their particular circumstances:
- Understand your IT set-up, assess your specific vulnerabilities to different threats, and document these (see Fig.1);
- Develop a strategy/approach to protect, detect and respond to cyber security threats (see the section on Practical steps/quick wins);
- Develop an Incident Response Plan and conduct routine testing (see section on Practical steps/“quick wins”);
- Cross-functional set-up: involve IT, legal/compliance, HR, external advisors; ensure senior management/board buy-in (cyber security awareness as part of company culture); all employees should “own” management of cyber risk;
- Develop security metrics and dashboards: to communicate progress (to internal and external stakeholders) and assess evolution of endogenous/exogenous threats;
- Ensure continuous awareness of cyber security risks at all employee levels and participate in cross-sectoral information sharing/collaboration (benchmarking against best practice, even against practice outside the financial services sector, can be an effective means of developing the most effective cyber risk management programme);
- Culture of continuous improvement.
It is important to recognise that cyber security is not a one-off exercise, but requires an ongoing effort to stay on top of the evolving nature of threats and adapt the cyber security strategy accordingly. In addition, regulators will continue to focus on cyber security, and managers will need to understand the evolving regulatory expectations. THFJ
The full version with all footnotes (and hyperlinks to external resources) is available at www.hfsb.org > Toolbox.
- Explore Categories
- Commentary
- Event
- Manager Writes
- Opinion
- Profile
- Research
- Sponsored Statement
- Technical